Word attack
This attack tries all possible variations of a given word, applying more mutations than in the dictionary attack with the "maximize efficiency" option selected.
Dictionary attack - Dictionary options
Press Add to add dictionary file(s) to the list, Remove to remove selected items, and Up/Down to reorder.
You can set Ignore password if it is shorter than 8 characters or longer than 64 characters. If this option is set, the program will check only those words from the wordlist that are 8 to 64 characters long and so comply with the wireless encryption standards. Since the wireless encryption standard does not permit passwords outside of the 8-64 characters range, we recommend keeping this option enabled.
Dictionary attack - Password mutation options
Select the name of the dictionary file, as well as the options that affect the speed and efficiency of the attack. See Dictionary mutations for more details.
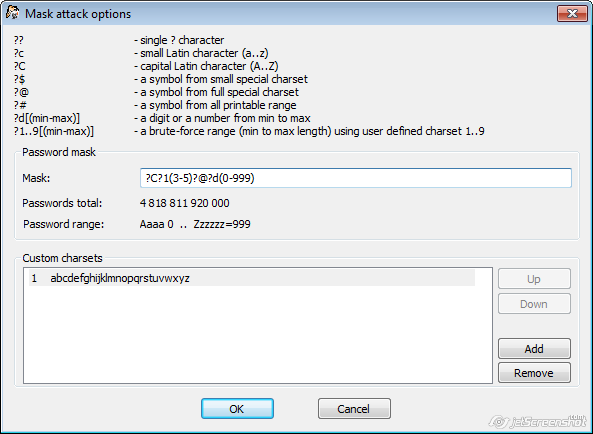
Mask attack
With the mask attack, you can check for passwords with a known/complex structure. In the Mask field, you can select a mask using the following options:
•?? - the '?' symbol itself
•?c - small Latin character (from 'a' to 'z')
•?C - large Latin character (from 'A' to 'Z')
•?$ - one of the special characters (small set): !@#$%^&*()-_+= and space
•?@ - one of the special characters (large/complete set): !\"#$%&'()*+,-./:;<=>?@[\]^_`{|}~ and space
•?# - any printable character with the code from 0x20 to 0x7F
•?d - one digit (from 0 to 9)
•?d(min-max) - a number from min to max.
•?1..9(min-max) - min..max characters from custom set
•?w[name.dic] - include dictionary words from dictionary with name english.dic
•?W[name.dic] - include dictionary words with case mutation of first letter
In order to use the last option, you should also create a custom character set; each set has its own number.
For example, assuming that you password is formed as follows:
- one capital letter
- from 3 to 5 small letters
- special character (from large set)
- from one to three digits
In that case, the mask is going to be as follows, assuming that the custom charset containing all small letters is created; if it is the only one, it will have the number 1:
?C?1(3-5)?@?d(0-999)
Once the mask is properly set, you will see the Password total (the total number of passwords that fits into this mask), and Password range (first and last passwords to be checked):
Combination attack
This attack allows to test passwords that consist of two words, each of them taken from the dictionary (word list). Select the dictionaries in the Dictionary 1 and Dictionary 2 fields; you can use the same file or different ones. The additional options are:
•Check upper- and lower-case combination
•Use word delimiters
•Use extra mutations
With the first option, the program will try to capitalize the first letter of each word, i.e. testing all four combinations. The second option (Use word delimiters) allows to set different characters (e.g. dash and underline) to be used as word delimiters. Finally, you can apply extra mutations to all resulting passwords (Dictionary mutations options will be used). The program tries to estimate the total number of passwords instantly, but it is not possible to calculate the exact number of mutations.
Hybrid attack
This attack is similar to the Dictionary attack described above, but all mutations are set by the user. Here you can select one or more dictionaries (wordlists), as well as several mutation rules. The rules are set in the *.rul files; here are the ones supplied with the program:
•all.rul - all rules (~82000)
•cases.rul - all possible case combinations (up to 15 character words)
•common.rul – common mutation rules
•custom.rul – default rules for custom attacks
•dups.rul – rules to search for passwords based on various duplicated words or characters
•dates.rul – date mutations
•keyboard.rul – rules to search for passswords based on all possible keyboard combinations
•l33t.rul – l33t 'language'
•numbers.rul – manipulations with numbers
•rockyou.rul – top rules based on various leaked passwords
The actual contents of a *.rul file starts with the [Rules] section (all text before this tag is ignored). The maximum length of one rule is 256 bytes. Maximum length of the output word as generated by the rule should not exceed 256 characters. A single line can contain several rules (except "aN"); they are processed from left to right. Several rules per line are allowed (except the "aN" rule); all text before the "[Rules]" line is considered as a comment. The maximal line length and maximal output word length are limited to 256 characters.
The syntax of mutations is fully compatible with Passcape and InsidePro software, and partially compatible with John the Ripper:
: Do nothing, use the original input word
{ Rotate word left: password -> asswordp
} Rotate right: password -> dpasswor
[ Delete the first character: password -> assword
] Delete the last character: password -> passwor
c Capitalize: password -> Password
C Lowercase the first character, uppercase the rest: password -> pASSWORD
d Duplicate: password -> passwordpassword
f Reflect: password -> passworddrowssap
l Convert to lowercase
K Swap the last two characters: password -> passwodr
q Duplicate all symbols: password -> ppaasssswwoorrdd
r Reverse: password -> drowssap
t Toggle case of all characters: PassWord -> pASSwORD
u Convert to uppercase
V Vowels elite: password -> PaSSWoRD
v Vowels noelite: password -> pASSWoRD
'N Truncate the word to N character(s) length
<N Reject the word if it is greater than N characters long. 0<=N<=35 (0,1,2,3,4,5,6,7,8,9,A,B,C..Z)
>N Reject the word if it is less than N characters long. 0<=N<=35 (0,1,2,3,4,5,6,7,8,9,A,B,C..Z)
+N Increment character at position N by 1 ASCII value
-N Decrement character at position N by 1 ASCII value
.N Replace character at position N with one at position N+1
,N Replace character at position N with one at position N-1
aN Check all possible symbol cases for the word. N is a maximal length of the word to apply this rule for. This rule CANNOT be used in conjunction with other ones!
DN Delete the character at position N
pN Copy word N times. N = 3 .. 9
TN Toggle case of the character at position N. N = 0 .. 9 for the position 0 - 9, N = A .. Z for the position 10 - 35
yN Duplicate first N characters
YN Duplicate last N characters
zN Duplicate the first character of the word N times. N = 1 .. 9
ZN Duplicate the last character of the word N times. N = 1 .. 9
$X Add character X to the end of the word
^X Insert character X at the beginning of the word
@X Remove all characters X from the word
!X Reject the word if it contains at least one character X
/X Reject the word if it does not contain character X
(X Reject the word if the first character is not X
)X Reject the word if the last character is not X
eX Extract a substring starting at position 0 and ending up before first occurrence of X character. Do nothing if X is not found.
EX Extract a substring starting right after the first found X character and till the end of the string. Do nothing if X is not found.
*MN Swap character at position M with character at position N
%MX Reject the word if it does not contain at least M instances of the character X
=NX Reject the word if the character at position N is not equal to the X
iNX Insert the character X in position N
oNX Overwrite a character in position N with the character X
sXY Replace all characters X with Y
xNM Extract a substring of up to M characters length, starting from position N. M = 1 .. 9 for the length equal to 1 - 9, M = A .. Z for the length equal to 10 - 35
SLN Bitwise shift left character at position N
SRN Bitwise shift right character at position N
Custom attack
Up to 5 dictionaries can be used, with specific mutations per dictionary. For example, let us take a password that may consist of a first and second name, with up to 4 digits in between. To break it, you will need three wordlists:
- First names
- All digits from 0 to 9999
- Second names
As we know nothing on the character case, we will use a rules file with simple mutations as follows:
[Rules]
l
u
c
C
Then apply it to the first and third wordlists only.